An application that applies string, method calls, function and variable obfuscation on javascript, JQuery enabled.
You still obfuscating like year 2000, using the eval() function? Or the nasty obfuscators around that have nothing to prove just rename the variable/function names then afterwards someone can easily read it using the famous http://jsbeautifier.org/ No way!
The application uses special text search functionality, doesnt know anything about javascript!
Platform : C# 2010
Operating System : Windows
 2000 /
2000 /
 XP /
XP /
 2003 /
2003 /
 Vista /
Vista /
 win7 (32bit)
win7 (32bit)
Requirements : v4 .NET framework
Filesize : 167kb
Restrictions : Encode only the first 10elements + occasionally adds dummy strings
Download
application rule :
v1.2 [27/11/2013]
+now obfuscate functions names
+array call is 'more secure' using poly engine!
*bug - when in #if condition# using a property equal with arithmetic example #if (word.length==0)# (aka line 44 on source)
-bug discover - when is a reference to an array ex. #items[2]# encrypts also the brackets should be fixed
v1.1 [24/11/2013]
+now obfuscate variables!
+trim single line comments
+export all code to one line
sample obfuscated with v1.2 https://www.pipiscrew.com/apps/ejuice/word_type_race.html
sample obfuscated with v1.1 https://www.pipiscrew.com/apps/ejuice
after (v1.2) :
before :
after (v1.0) :
online JS obfuscators :
http://jsutility.pjoneil.net/
http://www.xidea.org/project/jsa/
https://javascriptobfuscator.com/Javascript-Obfuscator.aspx
nodeJS -- https://github.com/javascript-obfuscator/javascript-obfuscator (online https://javascriptobfuscator.herokuapp.com/)
http://www.danstools.com/javascript-obfuscate/index.php
https://javascriptobfuscator.com/Javascript-Obfuscator.aspx
https://jscompress.com/
http://refresh-sf.com/
https://utf-8.jp/public/jjencode.html
https://github.com/MichaelXF/js-confuser
You still obfuscating like year 2000, using the eval() function? Or the nasty obfuscators around that have nothing to prove just rename the variable/function names then afterwards someone can easily read it using the famous http://jsbeautifier.org/ No way!

The application uses special text search functionality, doesnt know anything about javascript!
Platform : C# 2010
Operating System : Windows
Requirements : v4 .NET framework
Filesize : 167kb
Restrictions : Encode only the first 10elements + occasionally adds dummy strings
Download
application rule :
JavaScript:
//dont use variable declaration with const ex.
var x = 3;
//should be
var x;
x=3;v1.2 [27/11/2013]
+now obfuscate functions names
+array call is 'more secure' using poly engine!
*bug - when in #if condition# using a property equal with arithmetic example #if (word.length==0)# (aka line 44 on source)
-bug discover - when is a reference to an array ex. #items[2]# encrypts also the brackets should be fixed
v1.1 [24/11/2013]
+now obfuscate variables!
+trim single line comments
+export all code to one line
sample obfuscated with v1.2 https://www.pipiscrew.com/apps/ejuice/word_type_race.html
sample obfuscated with v1.1 https://www.pipiscrew.com/apps/ejuice
after (v1.2) :
JavaScript:
var _0x2IN6850;
var _0x2IN18890;
if (_0x2IN6850)
_0x2IN18890 = _0x2IN0[(9-4)];
else
_0x2IN18890 = _0x2IN0[~((-(2))-3)];
$(function() {
$(_0x2IN0[~~2])[_0x2IN0[(15^4)]]({css:_0x2IN0[(5+(-(2)))]});
});
function _0x2IN13930(url, itemOBJ, preserveColsArray, priority) {
console[_0x2IN0[(((-(0))+(8+5))-7)]](_0x2IN0[((2^(4+6))-7)] + url);
var _0x2IN35690 = new Firebase(url);
$[_0x2IN0[~~(3^(-(~9)))]](_0x2IN35690[_0x2IN0[(8^(-((7-9))))]](function(current_value) {
if (preserveColsArray) {
for (var i = 0; i < preserveColsArray[_0x2IN0[(-((-((6+~~2)))))]]; i++)
itemOBJ[preserveColsArray[i]] = current_value[preserveColsArray[i]];
}
return itemOBJ;
}))[_0x2IN0[((~1^~3)^5)]](function(x) {
console[_0x2IN0[(3-~(10^8))]](new Date() + _0x2IN0[(-((-(0))))]);
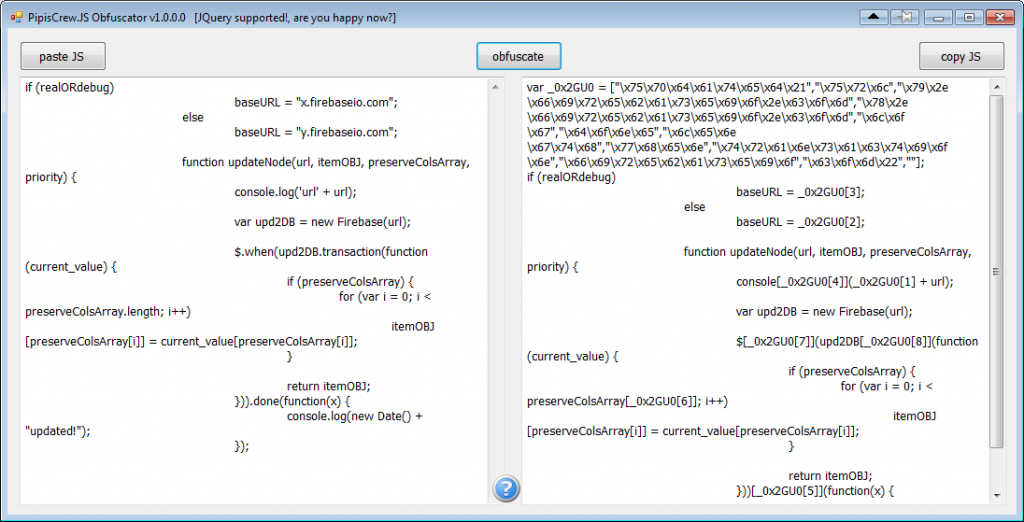
});before :
JavaScript:
if (realORdebug)
baseURL = "x.firebaseio.com";
else
baseURL = "y.firebaseio.com";
$(function() {
$("#oCOMPANY_descriptionLarge").jqte({css:"jqte_green"});
});
function updateNode(url, itemOBJ, preserveColsArray, priority) {
console.log('url' + url);
var upd2DB = new Firebase(url);
$.when(upd2DB.transaction(function(current_value) {
if (preserveColsArray) {
for (var i = 0; i < preserveColsArray.length; i++)
itemOBJ[preserveColsArray[i]] = current_value[preserveColsArray[i]];
}
return itemOBJ;
})).done(function(x) {
console.log(new Date() + "updated!");
});after (v1.0) :
JavaScript:
var _0x2MX0 = ["\x75\x70\x64\x61\x74\x65\x64\x21","\x75\x72\x6c","\x23\x6f\x43\x4f\x4d\x50\x41\x4e\x59\x5f\x64\x65\x73\x63\x72\x69\x70\x74\x69\x6f\x6e\x4c\x61\x72\x67\x65","\x6a\x71\x74\x65\x5f\x67\x72\x65\x65\x6e","\x79\x2e\x66\x69\x72\x65\x62\x61\x73\x65\x69\x6f\x2e\x63\x6f\x6d","\x78\x2e\x66\x69\x72\x65\x62\x61\x73\x65\x69\x6f\x2e\x63\x6f\x6d","\x6c\x6f\x67","\x64\x6f\x6e\x65","\x6c\x65\x6e\x67\x74\x68","\x77\x68\x65\x6e","\x74\x72\x61\x6e\x73\x61\x63\x74\x69\x6f\x6e","\x6a\x71\x74\x65","\x66\x69\x72\x65\x62\x61\x73\x65\x69\x6f","\x63\x6f\x6d\x22",""];
if (realORdebug)
baseURL = _0x2MX0[5];
else
baseURL = _0x2MX0[4];
$(function() {
$(_0x2MX0[2])[_0x2MX0[11]]({css:_0x2MX0[3]});
});
function updateNode(url, itemOBJ, preserveColsArray, priority) {
console[_0x2MX0[6]](_0x2MX0[1] + url);
var upd2DB = new Firebase(url);
$[_0x2MX0[9]](upd2DB[_0x2MX0[10]](function(current_value) {
if (preserveColsArray) {
for (var i = 0; i < preserveColsArray[_0x2MX0[8]]; i++)
itemOBJ[preserveColsArray[i]] = current_value[preserveColsArray[i]];
}
return itemOBJ;
}))[_0x2MX0[7]](function(x) {
console[_0x2MX0[6]](new Date() + _0x2MX0[0]);
});online JS obfuscators :
http://jsutility.pjoneil.net/
http://www.xidea.org/project/jsa/
https://javascriptobfuscator.com/Javascript-Obfuscator.aspx
nodeJS -- https://github.com/javascript-obfuscator/javascript-obfuscator (online https://javascriptobfuscator.herokuapp.com/)
http://www.danstools.com/javascript-obfuscate/index.php
https://javascriptobfuscator.com/Javascript-Obfuscator.aspx
https://jscompress.com/
http://refresh-sf.com/
https://utf-8.jp/public/jjencode.html
https://github.com/MichaelXF/js-confuser
